Master AI, Databases, Cloud Computing, and Programming with Expert-Led Training Courses
Master Databases, Programming, and Cloud Computing with our expert-led training courses. Learn in plain English through hands-on lessons, practical videos, and in-depth guides designed for all skill levels.

Web-Based, On-Demand Training
To attend our courses on Udemy, you just need a web browser and excitement to learn.

Certificate of Completion
After successfully completing our courses on Udemy, you get a certificate of completion.

Friendly Q&A
Don't worry if you get stuck during your learning path. Via our courses' Q&A, we can help you with any questions you might have.
Top Training Programs to Build Your Expertise

Introduction to Azure SQL Database for Beginners
Learn all about Azure SQL Database and Azure Server on Virtual Machines. Get started in no time via a comprehensive set of lectures and live demos.
Category: Azure Cloud Computing

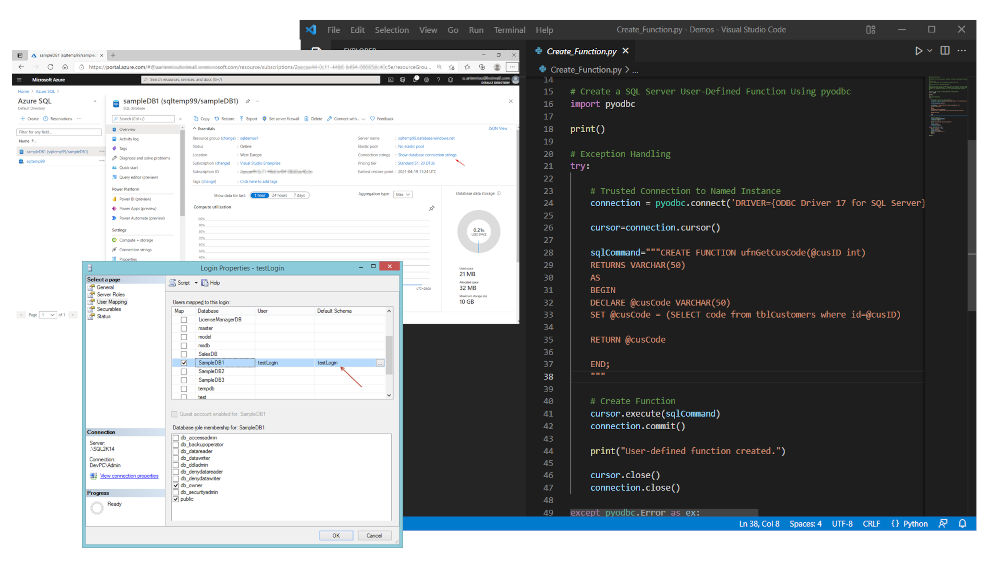
Working with Python on Windows and SQL Server Databases
Learn how to access and work with SQL Server databases, directly from your Python programs, by implementing Python data access programming.
Category: Data Access & Python

Essential SQL Server Administration Tips
Learn essential hands-on SQL Server Administration tips on SQL Server maintenance, security, performance, integration, error handling and more!
Category: SQL Server

SQL Server 2019: What’s New - New and Enhanced Features
Learn about the exciting new features and enhancements in SQL Server 2019 Database. Many live demos on Windows and Linux included!
Category: SQL Server

Essential SQL Server Development Tips for SQL Developers
Sharpen your SQL Server database programming skills via a large set of tips on T-SQL and database development techniques.
Category: SQL Server

Introduction to Computer Programming for Beginners
Learn the basics of Computer Programming and get started easily with a large set of programming languages (C++, C, Python, SQL, Java and C#).
Category: Programming

.NET Programming for Beginners - Windows Forms (C#)
Learn how to implement Windows Forms (WinForms) projects in Visual Studio with C#, multithreading and deployment packages.
Category: Programming & .NET

SQL Server Fundamentals - SQL Database for Beginners
The complete beginners guide that helps you get started with SQL Server, SSMS and Azure Data Studio fast and easy!
Category: SQL Server

Boost SQL Server Database Performance with In-Memory OLTP
Learn how you start using SQL Server's In-Memory optimization, also known as In-Memory OLTP and boost the performance of your data processes.
Category: SQL Server
Check our Full Course Collection
Thousands Have Upgraded Their Skills Through Our Training – Hear From Our Learners!
Very good and easy to follow. Nice tone of voice. Understandable, fast en precise. Overall nice job!
Really helped before starting my new job.
I really enjoyed the course. The instructor clearly explains all the concepts and the live demonstrations are very useful.
Very useful course. I like the way the instructor explains all aspects of data management in simple words.
Very informative and complete. Quite useful and thorough. Very well structured, with examples and easy to follow. Recommended.
About your Instructor
Greetings, I’m Artemakis Artemiou, a passionate educator and expert in Databases, Programming, Cloud Computing, Data Access, and the rapidly advancing field of Artificial Intelligence. My mission is to make these complex topics accessible to everyone, using clear, step-by-step guides and straightforward language.
With over 20 years of experience as a Senior Database & Software Architect, I specialize in database administration, development, performance tuning, architecture, and .NET development (C#). As a former Microsoft Data Platform MVP (2009–2018), I bring recognized industry expertise to my teaching, with a focus on making Databases and Artificial Intelligence understandable and applicable in real-world contexts. I hold certifications in both databases and Artificial Intelligence, ensuring that my courses are always at the forefront of technological advancements.
I founded the SQLNetHub and GnoelixiAI Hub communities, with a vision to share knowledge through expert-led training courses. These courses, available on Udemy, offer learners around the world the opportunity to gain hands-on experience in Databases, AI, and Cloud technologies through self-paced, practical learning.
Throughout my career, I have remained committed to fostering community growth, serving as President of the Cyprus .NET User Group and INETA Country Leader for Cyprus. These roles have allowed me to contribute to the global tech community, making knowledge-sharing a cornerstone of my work.
Join me on a continuous learning journey as we dive deep into Databases, Artificial Intelligence, Cloud Computing, and Programming. Together, we will make complex technology both accessible and enjoyable for everyone.