SQL Server Dynamic Data Masking Methods
- Default:
- Full masking according to the data types of the designated fields.
- Email: Masking method which exposes the first letter of an email address and the constant suffix “.com”, in the form of an email address. . aXXX@XXXX.com.
- Custom String:Masking method that exposes the first and last letters and adds a custom padding string in the middle. prefix,[padding],suffix
- Random: A random masking function for use on any numeric type to mask the original value with a random value within a specified range.
Strengthen your SQL Server Administration Skills – Enroll to our Online Course!
Check our online course on Udemy titled “Essential SQL Server Administration Tips”
(special limited-time discount included in link).
Via the course, you will learn essential hands-on SQL Server Administration tips on SQL Server maintenance, security, performance, integration, error handling and more. Many live demonstrations and downloadable resources included!

A Simple SQL Server Dynamic Data Masking Demo
A simple example of Dynamic Data Masking is to display only the last 4 digits of a phone number to the support personnel of an IT Department or don’t show the email address to unauthorized users, etc.
Now let’s proceed with a demo in order to see some examples of using Dynamic Data Masking.
/*
Demo: Dynamic Data Masking
*/
--Create a sample database
IF DB_ID('SampleDB_DataMasking') IS NULL
BEGIN
CREATE DATABASE SampleDB_DataMasking;
END
GO
--Use sample database
USE SampleDB_DataMasking;
GO
--Create sample table
CREATE TABLE tblEmployeesMasking
(
empName VARCHAR(250) ,
empPhoneNo VARCHAR(20) ,
empEmailAddress VARCHAR(100)
);
GO
--Populate sample table with data
INSERT INTO dbo.tblEmployeesMasking
VALUES ( 'John Clarck', '545-5478-1234', 'john.clark@example.com' ),
( 'Kostas Andreou', '878-8888-5678', 'kostas.andreou@example.com' ),
( 'Wei Xing', '673-5123-9101', 'wei.xing@example.com' );
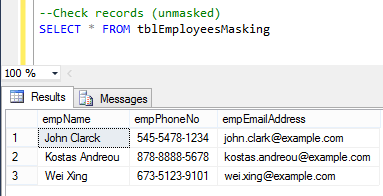
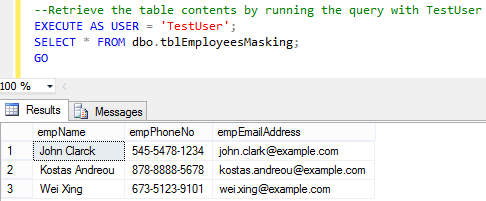
--Check records (unmasked)
SELECT * FROM tblEmployeesMasking
Output 1:
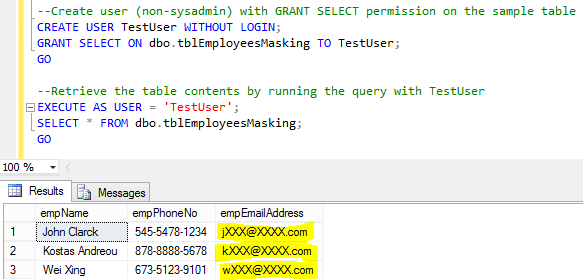
--Now let's mask the email address ALTER TABLE dbo.tblEmployeesMasking ALTER COLUMN empEmailAddress VARCHAR(100) MASKED WITH (FUNCTION = 'email()'); Let's check again the records of the table, this time using a non-sysadmin user. --Create user (non-sysadmin) with GRANT SELECT permission on the sample table CREATE USER TestUser WITHOUT LOGIN; GRANT SELECT ON dbo.tblEmployeesMasking TO TestUser; GO --Retrieve the table contents by running the query with TestUser EXECUTE AS USER = 'TestUser'; SELECT * FROM dbo.tblEmployeesMasking; GO
Output 2:
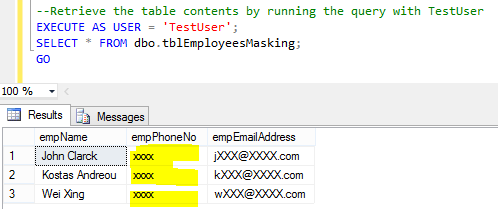
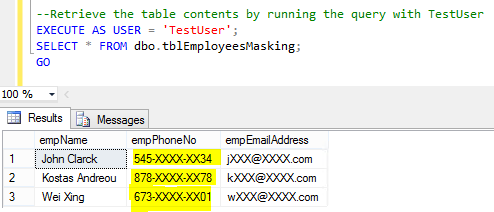
REVERT; GO --Let's mask the phone number with default ALTER TABLE dbo.tblEmployeesMasking ALTER COLUMN empPhoneNo VARCHAR(100) MASKED WITH (FUNCTION = 'default()'); Let's check the records of the table using a non-sysadmin user. --Retrieve the table contents by running the query with TestUser EXECUTE AS USER = 'TestUser'; SELECT * FROM dbo.tblEmployeesMasking; GO
Output 3:
REVERT; GO --Remove masking ALTER TABLE dbo.tblEmployeesMasking ALTER COLUMN empPhoneNo VARCHAR(100) --Let's mask the phone number with custom function ALTER TABLE dbo.tblEmployeesMasking ALTER COLUMN empPhoneNo VARCHAR(100) MASKED WITH (FUNCTION = 'partial(3,"-XXXX-XX",2)');
--Retrieve the table contents by running the query with TestUser EXECUTE AS USER = 'TestUser'; SELECT * FROM dbo.tblEmployeesMasking; GO
Output 4:
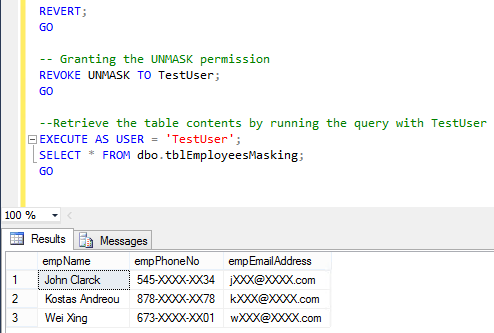
REVERT; GO -- Granting the UNMASK permission GRANT UNMASK TO TestUser; GO Let's check the records of the table within the context of 'TestUser': --Retrieve the table contents by running the query with TestUser EXECUTE AS USER = 'TestUser'; SELECT * FROM dbo.tblEmployeesMasking; GO
Output 5:
Discussion
Dynamic Data Masking is a significant feature in SQL Server 2016 and Azure SQL Database. As you can see from the above examples it is very easy to use it and it can really help you when it comes to Security and Compliance regarding yours or your organization’s most valuable asset: the data.
Featured Online Courses:
- SQL Server 2022: What’s New – New and Enhanced Features
- Working with Python on Windows and SQL Server Databases
- Introduction to Azure Database for MySQL
- Boost SQL Server Database Performance with In-Memory OLTP
- Introduction to Azure SQL Database for Beginners
- Essential SQL Server Administration Tips
- SQL Server Fundamentals – SQL Database for Beginners
- Essential SQL Server Development Tips for SQL Developers
- Introduction to Computer Programming for Beginners
- .NET Programming for Beginners – Windows Forms with C#
- SQL Server 2019: What’s New – New and Enhanced Features
- Entity Framework: Getting Started – Complete Beginners Guide
- Data Management for Beginners – Main Principles
- A Guide on How to Start and Monetize a Successful Blog
References:
- MSDN Library Article: What’s New in SQL Server 2016
- MSDN Library Article: Dynamic Data Masking
- Microsoft Azure Document: Get started with SQL Database Dynamic Data Masking
See also…
- SQL Server 2016 Top Features
- What is Data Security and which are its Main Characteristics?
- SQL Server 2022: What’s New – New and Enhanced Features (Course Preview)
- An existing History Table cannot be specified with LEDGER=ON – How to Resolve
- SQL Server 2022 Overview: A Hybrid Data Platform
- Azure Synapse Link in SQL Server 2022
Subscribe to our newsletter and stay up to date!
Check our online courses!
Check out our eBooks!
Rate this article:
Reference: SQLNetHub.com (https://www.sqlnethub.com)
© SQLNetHub
Artemakis Artemiou, a distinguished Senior Database and Software Architect, brings over 20 years of expertise to the IT industry. A Certified Database, Cloud, and AI professional, he earned the Microsoft Data Platform MVP title for nine consecutive years (2009-2018). As the founder of SQLNetHub and GnoelixiAI Hub, Artemakis is dedicated to sharing his knowledge and democratizing education on various fields such as: Databases, Cloud, AI, and Software Development. His commitment to simplicity and knowledge sharing defines his impactful presence in the tech community.